AWS
Intro to AWS Core Services and how to hack them
Last updated: May 4th, 2023Intro
Accounts
- AWS Account
- Container for resources
- Unique 12-digit ID
- Security boundary, root creds are the only way to access control plane
- Root User
- One email = one root user
- IAM superuser
- AWS Organisations root setup commonly results in a root user with weak passwords and no MFA
- Quit Riot is a tool to enumerate valid root user email addresses
IAM
- IAM engine evaluates access granted to IAM principles through a series of logic statements that begin with implicit deny and are evaluated to explicit deny or explicit allow.
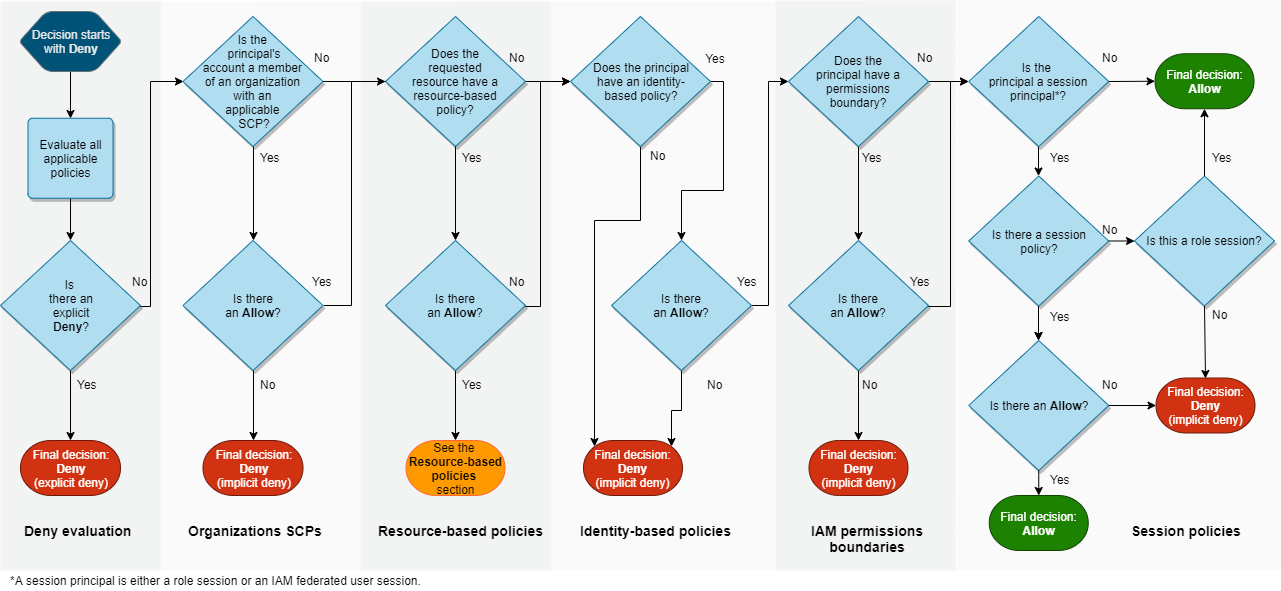
- IAM roles
- AWS principles that have permissions
- assume-role/switch-role
- Allow other identities to gain privileges of another IAM role as determined by the "assume-role trust policy"
- Supports SAML and OpenID
- Identity Center allow IdP access to permission sets
Organizations
- Hierarchical
- Organizational policies can be used to restrict child accounts
VPC
- Allow network segmentation
- Default VPC Service Caps
- DNS Resolver @ 169.254.169.253
- NTP @ 169.254.169.123
- KMS Service for Windows Licensing @ 169.254.169.250-1
- EC2 @ 169.254.169.254
- ECS @ 169.254.170.2
S3
Terms and Concepts
- Bucket
- A flat file storage system that can hold objects (files) up to 5TB
- Pseudohierarchical folders are used but buckets can not contain other buckets
- Access Controls
- s3:GetObject (read) and s3:PutObject (write)
- Access Control Lists
- S3 Buckets before November 2021 used ACL's, they are recommended to be disabled but some still use them now.
- Identity-based
- Bucket Policies
- More human-readable syntax
- Resource-based
Public S3 Buckets
- Until 2018, new buckets were public by default.
- Many ways to find
- Search Engines
- Web page source
- DNS recon
- Subdomain recon
- Naming Conventions
- You can download an s3 bucket using the aws cli
aws s3 sync s3://{bucket-name} . --no-sign-request