C182 - Intro to IT
I started by taking the PLG, anything that was weak, I would write down and review, after the initial review I took the Practice Assessment, anything less than exemplary I would review and then register for the exam.
Last updated: May 4th, 2023
Notes
Compilers and Interpreters
- Compilers
- Translate source code into machine code, if there is an error, the user must fix the error before the program will compile
- C, C++, Java, and C# are compiled languages
- Interpreters
- Translate source code into machine code line by line, if the interpreter runs into an error, the interpreter will stop and the user can then fix the error. The interpreter will then continue.
- Python, Ruby, and JavaScript are interpreted languages
Relational, Flat-File, and Hierarchical Databases
- Relational Databases
- Stores data in tables
- Tables are made up of rows and columns
- Useful for storing data that has a relationship with other data
- Flat-File Databases
- Stores data in a single file
- Each record is stored on a separate line
- Data may have an inferred relationship, but the database format does not make it explicit
- Hierarchical Databases
- Stores data in a tree structure
- Each record is stored in a node
- Each node can have multiple children
- Each node can have one parent
SQL Commands
- Select
- Used to select data from a database
- Can be used to select all data from a table or to select specific data
- Project
- Used to select specific columns from a table
- Can be used to rename columns
- Union
- Used to combine the results of two or more select statements
- Each select statement must have the same number of columns
- Join
- Used to combine rows from two or more tables, based on a related column between them
- Results in a table with as many rows as there are matches between the tables
Topologies
Bus
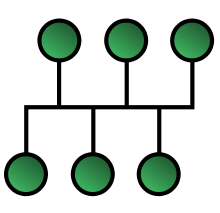
- Devices are connected to a central cable
- Low cost
- Easy to install
- Easy to extend with a repeater
- Collision domain is the entire network
- Fault isolation is difficult
Star

- Devices are connected to a central hub
- Devices can be added or removed without disturbing the network
- Works well under heavy load
- Single point of failure
Ring
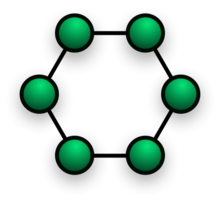
- Devices are connected in a ring
- Performs better than bus under heavy loads
- Easy fault isolation
- Adding devices can affect the network
- One malfunctioning device can affect the entire network
Mesh
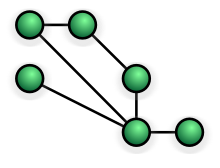
- Devices are connected to each other
- Each device is in its own collision domain
- High fault tolerance
Project Management
- Initiation
- Project charter is created
- Business case and needs analysis are performed
- Project stakeholders provide input
- Planning
- Roadmap is developed
- Goals are defined using SMART and CLEAR frameworks
- SMART
- SMART is an acronym that stands for Specific, Measurable, Achievable, Relevant, and Time-Bound. It is used to define project goals.
- CLEAR
- CLEAR is an acronym that stands for Cost, Legal, Ethical, Acceptable, and Realistic. It is used to define project goals.
- Scope is defined
- Risk is identified
- Execution
- Kickoff meeting is held
- Project team is formed
- Resources are allocated
- Timetable is monitored
- Closure
- Project is completed
- Financial reports are completed
- Strengths and weaknesses are evaluated
Project Risks
- Scope creep
- uncontrolled change of a project’s scope, typically adding tasks and increased, unplanned costs to the project
- Budget risk
- budget control issues, such as underestimated or improper allocation of cost
- Resistance to change
- departments and individuals resist organizational changes resulting from the project
- Resource risk
- inability to secure sufficient resources for the project
- Contract risk
- a vendor fails to deliver on contractual obligations
- Disputes or disagreements between project participants
- Project dependencies
- especially when completion of some tasks is dependent on the completion of other tasks
- Project assumptions risk
- when assumptions about the project are invalidated during project development
- Benefit shortfall
- the project meets the requirements but delivers fewer benefits than outlined in the business case
- Requirements quality risk
- requirements have not been properly validated or documented
- Force majeure risk
- the chance of a major negative event beyond human control, such as a natural disaster
Project Development Methodologies
Waterfall
- Linear
- Sequential
- Phased
Agile
- Continuous
- Daily cooperation between developers and business stakeholders
- Mantains a working product at all times
Extreme Programming
- Agile
- Continuous integration
- Test-driven development
- Pair programming
- Refactoring
- Continuous testing
- Continuous deployment
- Continuous feedback
- Continuous improvement
Government Regulations
- Privacy Act of 1974
- Privacy Act of 1974 is a federal law that protects the privacy of personal information.
- Family Educational Rights and Privacy Act (FERPA) 1974
- FERPA 1974 is a federal law that protects the privacy of student information.
- Electronic Communications Privacy Act of 1986
- Electronic Communications Privacy Act of 1986 is a federal law that protects the privacy of electronic communications.
- Computer Matching and Privacy Protection Act of 1988
- Computer Matching and Privacy Protection Act of 1988 is a federal law that limits the use of DBs and other matching programs to match data across DBs
- Driver's Privacy Protection Act of 1994
- Driver's Privacy Protection Act of 1994 is a federal law that prohibits states from selling data obtained in the process of registering drivers
- Health Insurance Portability and Accountability Act of 1996
- Health Insurance Portability and Accountability Act of 1996 is a federal law that protects the privacy of health information.
- Digital Millennium Copyright Act of 1998
- Digital Millennium Copyright Act of 1998 is a federal law that makes it illegal to violate copyrights by sharing digital material.
- Digital Signature and Electronic Authentication Act of 1998
- SEAL permits the use of digital sigs in financial transactions
- Security Breach Notification Laws
- Security Breach Notification Laws are laws that require companies to notify customers when their data has been compromised.