C480 - Networks (Network+)
For this class, I started by taking all of the network+ ExamCompass tests, anything below a 90% I would write down the correct answer and some context below using Professor Messers videos. Finally, I would take Jason Dion's practice test on Udemy, after getting a 90% on the first test I signed up for the exam.
Last updated: April 4th, 2023
Notes:
1 - Networking Concepts
1.1 - OSI Model
- physical, bit, cables, loopbacks, punchdowns, hubs, repeaters
- data link, frame, mac, switch, ethernet
- network, packet, ip, port numbers, router
- transport, segment/datagram, udp/tcp,
- session, auth
- presentation, encryption/decryption, compression, format translation
- application, http, ftp, smtp, etc.
1.2 - Network Topologies
- WAN Termination
- Demarcation Point
- Where you connect to the outside world
- Smartjack
- NIU - Device determines the demarc
1.3 - Cables
- Cable Management
- Copper Patch Panel
- Provide a centralized location for cable management and make it easy to troubleshoot network issues
- Consists of multiple ports that can be connected to individual network devices such as computers, switches, and routers
- 66 block
- A patch panel for analog voice
- Wire and a punch-down tool
- Replaced by 110 blocks
- 110 block
- Patch Category 5 and Category 6 cables
- Krone block
- Commonly used in Europe and is an alternative to the 110 block
- BIX(Building Industry Cross-connect)
- GigaBIX performance is better than the Category 6 cable standard
- Ethernet Standards
- Ethernet
- 10BASE-T
- Two pair, Category 3 cable minimum
- 100m
- 100BASE-TX
- Category 5 or better twisted pair copper - two pair
- 100m
- 1000BASE-T
- A shift to using all four pair
- 4-pair balanced twisted-pair
- 10GBASE-T
- Frequency use of 500 MHz
- Category 6; Unshielded: 55 meters, Shielded: 100 meters
- Category 6A (augmented); Unshielded or shielded: 100 meters
- 40GBASE-T
- Category 8 cable; Up to 30 meters
- Fiber
- 100BASE-FX
- Pair of multimode fiber - Same fiber as FDDI
- 400 meters (half-duplex), 2 kilometers (full-duplex)
- 100BASE-SX
- A less-expensive version of 100BASE-FX
- LED optics, 300 meters maximum distance
- 1000BASE-SX
- Gigabit Ethernet using NIR (near infrared) light
- 220 meters to 500 meters
- 1000BASE-LX
- Gigabit Ethernet using long wavelength laser
- Multi-mode fiber to 550 meters
- Single-mode fiber to 5 kilometers
- 10GBASE-SR
- 26 to 400 meters, depending on the fiber
- 10GBASE-LR
- 10 kilometers maximum range
- WDM
- Wavelength Division Multiplexing
- CWDM, DWDM
1.4 - IP Subnetting
IPv4
- Binary Math

- Calculating Subnets and Hosts
- Determine Classful range
- Identify interesting octet
- Calculate Magic number
- Calculate host range
- Identify net addy
- Identify broad addy
- IP: 165.245.77.14, Mask: 255.255.240.0
- If mask is 255, copy IP
- If mask is 0, copy mask
- The interesting octet is remaining octet
- Subtract interesting octet from 256
- 256-240=16
- The magic number is 16, determine where the IP falls in the multiple of the magic number, in our case: 16, 32, 48, 64, 80...
- Our interesting octet IP is 77 which would fall between 64 and 80 so we go with the lowest, 64.
- Classes
- Class A
- The first octet is reserved for network ID, and the remaining three octets are available for host ID
- This provides a large address space of up to 126 networks, each with up to 16,777,214 hosts
- Range: 1.0.0.0 to 126.0.0.0
- Class B
- The first two octets are reserved for network ID, and the remaining two octets are available for host ID
- This provides a smaller address space of up to 16,384 networks, each with up to 65,534 hosts
- This provides an even smaller address space of up to 2,097,152 networks, each with up to 254 hosts
- Range: 128.0.0.0 to 191.255.0.0
- Class C
- The first three octets are reserved for network ID, and the remaining octet is available for host ID
- This provides an even smaller address space of up to 2,097,152 networks, each with up to 254 hosts
- Range: 192.0.0.0 to 223.255.255.0
Binary Translation Subnetting
Magic Number Calculator
IPv6
- Abbreviate groups of zeros with a double colon ::, with only one abbreviation allowed per address, and leading zeros are optional
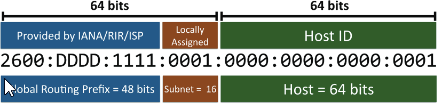
- 128 bits
- IPv6 tunneling options:
- 6 to 4 addressing
- 4in6
- Teredo/Miredo
- Dual-stack routing
- NDP (Neighbor Discovery Protocol) in IPv6 replaces ARP for MAC address discovery.
- NDP includes features such as SLAAC for automatic IP configuration and DAD for preventing duplicate IPs without dhcp server.
- RS/RA messages in NDP are used for router discovery.
- ICMPv6 adds NDP for finding routers with unsolicited RA messages.
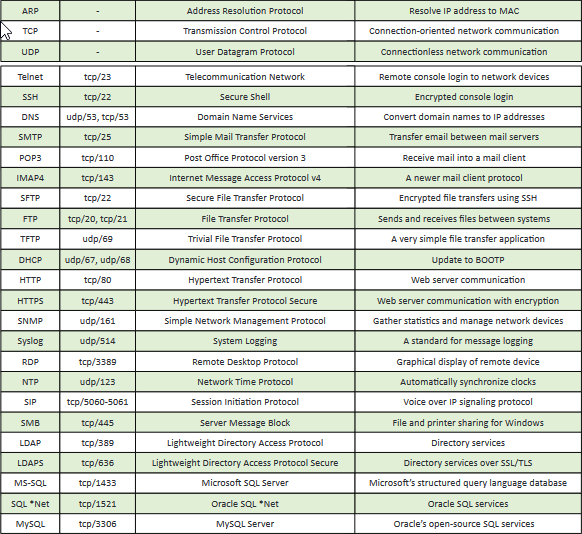
1.5 - Common Ports
2 - Network Implementations
2.2 - Routing
- Dynamic Protocols
- Distance-Vector
- Counts hops automatically
- Good for small networks
- RIP, EIGRP
- Link-state
- Related to connectivity
- Large networks
- OSPF
- Hybrid
- BGP - Border Gateway Protocol
2.3 - Network Switching
- Ethernet Overview
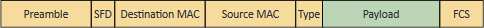
- MAC
- Organizational ID + NIC ID
- Half-Duplex
- Send OR recieve at anytime
- Full-Duplex
- Send AND recieve at anytime
- CSMA/CD
- Carrier Sense
- Mulitple Access
- Collision Detect
- Switching Overview
- A switch forwards or drops frames based on the dest mac and constantly updates its mac list based on incoming traffic
- Switches maintain a loop-free env with STP
- Blocking
- Listening
- Learning
- Forwarding
- Disabled
- 802.1D
- 802.1w
- Faster
- ARP allows you to determine MAC with IP
- NDP is ARP for IPv6
- SLAAC - DHCP w/o server
- DAD - dupe detector
- RS, RA, NS, NA
- VLAN Trunking
- 802.1Q
- Adds vlan to eth frame
- Commonly used for voice
- Helps avoid congestion
2.4 - Wireless Networking
Wireless Standards
- 802.11a
- 5GHz
- 54Mbits/s
- Not good at penetrating walls
- 802.11b
- 2.4GHz
- 11Mbits/s
- Frequency conflicts
- 802.11g
- 2.4GHz
- 54Mbits/s
- 802.11n
- 5GHz or 2.4GHz
- 600Mbits/s
- MIMO
- 2009
- 802.11ac
- 5GHz
- Eight MU-MIMO streams
- 7Gbits/s
- 2014
- 802.11ax
- 5GHz or 2.4GHz
- Eight bi-directional MU-MIMO streams
- 9.6Gbits/s
- OFDMA
- Similar to cell
- good for density
- 2021
Wireless Encryption
- WPA
- WPA2 and CCMP
- Counter Mode with Cipher Block Chaining
- AES encryption
- Message Integrity Check with CBC-MAC
- WPA3 and GCMP
- Galois Counter Mode
- MIC with GMAC
- SAE
- Creates a shared session key without sending across network
- Different session key with same PSK
Cellular
- 2G
- GSM
- CDMA
- 3G
- 4G
- Converged GSM and CDMA
- Based on GSM and EDGE
- 5G
- 10Gbits
3 - Network Operations
3.1 - Statistics and Sensors
SNMP
- Database containing object ids (OIDs)
- Devices are polled over udp 161, snmp traps communicate over udp 162
Logs and Monitoring
- Interface Errors
- Runts
- less than 64 bytes
- collision?
- Giants
- more than 1518 bytes
- CRC error
- may indicate bad cable
3.2 Logs and Monitoring
Plans and Procedures
- NIST SP800-61
- IR lifecycle
- Main Distribution Frame (MDF)
- Central Point of Network
- Intermediate Distribution Frame (IDF)
- Strategic distribution point
- ANSI/TIA/EIA 606
- Cable management
4 - Network Security
4.2 - Common Attacks
- VLAN Hopping
- Switch Spoofing
- Malicious user pretends to be a switch and sends a trunk negotiation
- Double Tagging
- Crafting a packet with two VLAN tags, the native tag gets removed, packet gets forwarded to target
4.3 - Network Hardening
- RA Guard
- Switches can validate the RA messages
- A rogue device could pretend to be a router
- Port Security
- Prevent unauthorized users from connecting to a switch interface based on MAC
- Configure a maximum number of source MAC addresses on an interface
- DHCP snooping
- IP tracking on a layer 2 device
- Switch watches for DHCP conversations asd adds a list of untrusted devices to a table
- Dynamic ARP inspection (DAI)
- Prevent on-path attacks
- Relies on DHCP snooping
- Intercept all ARP req and resp
5 - Network Troubleshooting
5.1 - Methodology
- Identify the problem
- Establish a theory of probable cause
- Test the theory
- Establish a plan of action
- Implement the solution or escalate as necessary
- Verify functionality
- Document
5.2 - Cable
- Plenum
- HVAC
- Toxic fumes if burned
- Fire-rated
- PVC
- Low-smoke polyvinyl chloride
- FEP
- Fluorinated ethylene polymer
5.3 - Tools
Hardware
- Cable Crimper
- A tool used to terminate Ethernet cables by attaching connectors to the cable ends.
- Punch-down
- A technique used to terminate twisted pair cables on patch panels or keystone jacks in a structured cabling system.
- Tone Generator
- A device used to trace and identify cables by sending a tone through the cable, which can be detected using a tone probe or tracer.
- Loopback Plug
- A device used to test the functionality of a network port by creating a loopback connection.
- TDR/OTDR
- Time-Domain Reflectometer (TDR) or Optical Time-Domain Reflectometer (OTDR) are tools used to troubleshoot and test the integrity of network cables, particularly in fiber optic networks.
- Multimeter
- A versatile tool used to measure various electrical parameters, such as voltage, current, and resistance, which can be helpful in diagnosing network equipment issues.
- Cable Tester
- A device used to verify the connectivity and performance of network cables by testing for continuity, short circuits, and open circuits.
- Taps and Port Mirrors
- Network monitoring tools used to capture and analyze network traffic for troubleshooting, performance monitoring, and security purposes.
- Light Meter
- A tool used to measure the intensity of light in fiber optic networks to ensure proper signal transmission and detect potential issues.
- Spectrum Analyzer
- A device used to analyze and measure the frequency spectrum of signals in a network to identify and troubleshoot interference, signal quality, and performance issues.
- Fusion Splicer
- A device used to join two fiber optic cables together by melting and fusing their ends, creating a low-loss connection.
Command-Line Tools
- ping - Test reachability
- ping <ip address> - Test reachability to a TCP/IP address
- ping -t <ip address> - Ping until stopped with Ctrl-c
- ping -a <ip address> - Resolve address to a hostname
- ping -n <count> <ip address> - Send # of echo requests
- ping -f <ip address> - Send with Don’t Fragment flag set
- arp - Address resolution protocol information
- arp -a - View the local ARP table
- netstat - Display network statistics
- netstat -a - Show all active connections
- netstat -b - Show binaries
- netstat -n - Do not resolve names
- Route
- View the device's routing table to determine the path that packets will take.
- Windows: route print
- Linux and macOS: netstat -r
- Tcpdump
- Capture packets from the command line.
- Available in most Unix/Linux operating systems, included with Mac OS X, and available for Windows (WinDump).
- Apply filters and view captured packets in real-time.
- Written in standard pcap format.
5.4 - Common Issues
Wireless
- Overlapping channels: Use a wireless analyzer to avoid interference from other access points.
- Attenuation: Wireless signals weaken as you move farther from the antenna. Measure attenuation with a Wi-Fi analyzer and control power output or use higher gain receive antennas.
- Wrong SSID: Confirm correct SSID settings as multiple SSIDs can be confusing. Check current connection status for the right SSID.
- Wrong passphrase: Check wireless authentication methods and ensure correct passphrase is used for connection.
- Security type mismatch: Ensure client matches access point encryption settings, upgrade legacy equipment if needed, and migrate from WEP to WPA2/3.
- Incorrect antenna placement: Check access point locations and channel settings to avoid interference and slow throughput.
- Captive portal: Authenticate to network through captive portal page with username/password. Check for authentication timeout and back-end process.
- Client disassociation: Identify and remove device causing denial of service attack through 802.11 frame information capture with Wireshark.
Network
- Half-duplex Ethernet: Collisions are normal and can be caused by heavy utilization, interface configuration issues, or hardware issues.
- Broadcast storms: Large numbers of broadcasts can impact performance, and troubleshooting can involve packet capture and separating the network into smaller broadcast domains.
- Duplicate MAC addresses: Not common but can occur due to mistakes or on-path attacks, and can cause intermittent connectivity.
- Duplicate IP addresses: Static address assignments, overlapping DHCP servers, or rogue DHCP servers can cause intermittent connectivity and IP address conflicts.
- Multicast flooding: Switches forward multicast traffic to all ports, consuming resources on remote devices and using bandwidth and switch processing time.
- IGMP Snooping: Hosts and routers use IGMP to direct multicast transmissions, and switches can intelligently forward multicasts to specific devices by enabling IGMP snooping.
- Asymmetric Routes: Traffic follows different paths on egress and ingress, which can be challenging to troubleshoot and may result in dropped sessions. Traceroute can help identify potential asymmetric routes.
- Switching Loops: Spanning Tree Protocol is often configured to prevent switching loops, which can cause broadcast storms. Broadcasts and multicasts are sent to all switch ports, making it difficult to identify loops at the MAC address level.
- Routing Loops: Misconfigured routes can result in routing loops, where routers send traffic back and forth indefinitely. Traceroute can help identify and resolve routing loops.
- Missing Route: If a route to the destination network does not exist, packets will be dropped. Checking and modifying routing tables in each L3 device can resolve this issue.
- Rogue DHCP Server: Rogue DHCP servers can assign invalid or duplicate IP addresses, causing connectivity issues. Enabling DHCP snooping and using authorized DHCP servers can help prevent rogue DHCP servers.
- Exhausted DHCP Scope: If DHCP server runs out of IP addresses in its scope, clients may receive APIPA addresses, resulting in limited local subnet communication. Monitoring and adding more IP addresses, lowering lease time, or using IP address management tools can help resolve this issue.
- IP Configuration Issues: Issues with IP address, subnet mask, gateway, or DNS settings can cause communication problems. Checking documentation, monitoring traffic, and confirming subnet mask and gateway settings can help troubleshoot IP configuration issues.
- Low Optical Link Budget: Fiber networks rely on transmission of light, and attenuation can occur over long distances or with dirty connectors. Using a light meter and checking equipment documentation can ensure sufficient light for proper network functioning.
- Certificate Issues: Security alerts and invalid certificates may indicate expired or improperly signed certificates. Checking certificate details, domain names, and time/date settings can help resolve certificate issues.